Single Sign-On (SSO)
Introduction
Goal
Understand how Bloomreach Experience Manager's architecture supports single sign-on integration in enterprise environments.
Background
Organizations who implement Bloomreach Experience Manager in their enterprise environment may want to integrate with their existing single sign-on (SSO) solution. This page explains how Bloomreach Experience Manager's system architecture supports SSO integration. Specific integrations are described separately.
Enterprise SSO-Enabled Architecture
The deployment diagram below shows Bloomreach Experience Manager's SSO-enabled system architecture:
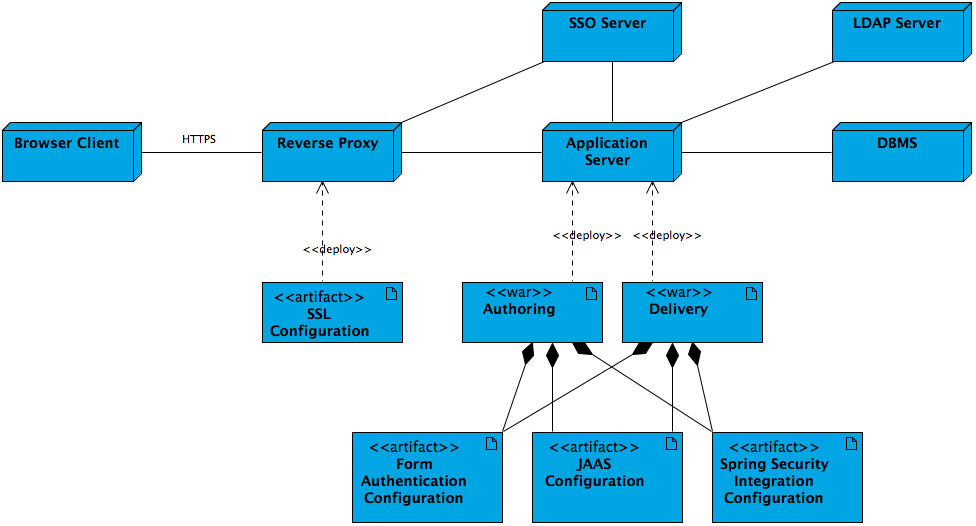
- Typically the HTTPS connection for browser clients is configured and enabled in the reverse proxy layer (Apache Web Server).
- Typically the reverse proxy redirects client requests to the enterprise SSO server for authentication. Once authenticated, the request is redirected back with a valid security token.
- Applications running on the application server can access the enterprise SSO server to validate security tokens if needed.
- Alternatively the authoring and delivery applications running on the application server can also authenticate users against the LDAP server if configured.
- Alternatively the authoring and delivery applications running on the application server can also authenticate users through either form authentication, JAAS or Spring Security integration. Spring Security integration is capable of integrating with an enterprise SSO server seamlessly.
Requests to Exclude
Requests to the following paths should not be redirected to the enterprise SSO server:
- /cms/ws/indexexport (Lucene index export)
- /cms/ping (CMS Ping Filter)
Specific Integrations

